Information Security Education
The Employee Checklist for Information Security acts as a guide to assist individuals in safeguarding University information resources in an appropriate manner. More detailed information may be found in the Standards and Guidelines associated with University Policy 311 Information Security.
Security Awareness and Reporting
The University’s recommended Security Awareness Training equips participants with information security best practices and references to related University IT policies. The training includes several videos, ranging from one to five minutes each. Closed captioning is available.
Did you know you have the responsibility to report incidents to OneIT? If you receive an email you believe may be phishing, do not send a reply, click on a link, or open any attachments. Forward the email to reportspam-group@charlotte.edu, and OneIT will investigate. If you believe you may have fallen victim to a phishing email, change your NinerNET password and contact the OneIT Service Desk.
Protect Passwords and Access
You should treat your password as confidential information and not divulge it to anyone. Do not reuse your NinerNET password (or any password, ever) for another account. Do not store password information in a file unless you have applied a strong password on the file. Protect confidential and sensitive information on your device by locking, logging off, or shutting down. Lock your device if you’re leaving your workspace for the water cooler, log off if you’re heading to lunch, and shut down if you’re going home for the evening.
Use Two-Factor Authentication
Duo two-factor authentication adds an extra layer of protection to your NinerNET account by requiring two factors to verify your identity – “something you know” like your password and “something you have” such as your phone. Duo is a very effective method for preventing unauthorized access to many University systems, including Gmail, My.charlotte, Banner, Dropbox, Kronos, and Canvas. Students, employees, sponsored guests, and Emeriti Faculty are required to sign up for DUO two-factor authentication.
Sharing and Handling Files, Documents, and Data
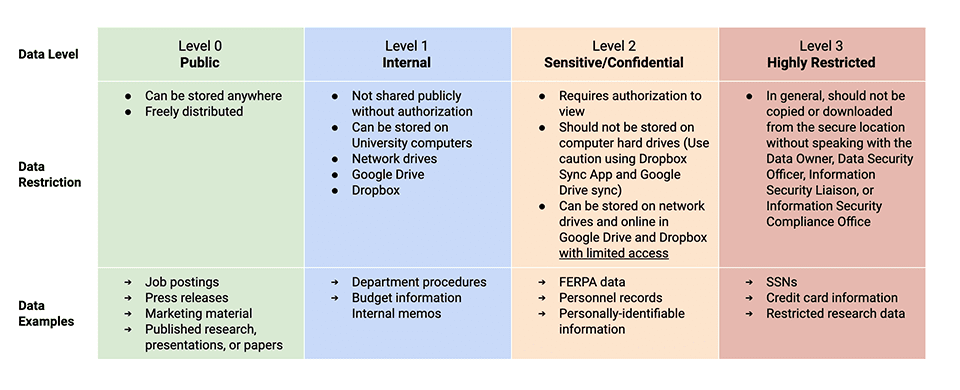
Grasp the four levels of data classification and understand where data may be stored based on them. Limit access to those who have a need to know and are authorized to view the data. Never store confidential or sensitive University information on non-University cloud services. Delete files in the Downloads folder and empty the Recycle Bin frequently to ensure that sensitive/confidential University information is not stored in these locations.
If you need to transfer sensitive University information, first check the restrictions on how the data is to be handled, which may be governed by the Guideline for Data Handling, a Data Security Plan, or legal, regulatory or contractual restrictions. If you plan to transfer sensitive University information to an external entity, confirm with the appropriate responsible party that agreements are in place between the University and said entity. If you share a password-protected file with an authorized person/entity, the password must be sent separately.
Remote Access Device
The University’s secure VPN can add an extra layer of protection when accessing University resources from a remote location. If you plan to work from a mobile device or personal tablet or computer, you must set a password, PIN, or swipe pattern for access. Additionally, be sure to adhere to the policies governing information security and acceptable use as well as the corresponding standards and guidelines. If you plan to travel to another country with a University or personal laptop, tablet, or smartphone, please contact the Export Control department and Economic Development Office.
Copiers, Printers, and Fax Machines
Use copiers, printers, and fax machines that are located in secure areas if you must transmit sensitive University information. Work with OneIT or our Information Security Liaison to ensure University devices are configured appropriately to secure University information in transmission. Do not use non-University devices to copy, print, or fax non-public University information.
Hardware Disposal, Reassignment, or Surplus
Ensure that data is erased before reassigning University-owned hardware and/or media within a department. Work with our Information Security Liaison to ensure that data has been properly removed by destroying, purging, or clearing it, based on the Guideline for hardware and media disposal, before disposal or surplus.
